|
|
 |
 |
 |
 |
 |
 |

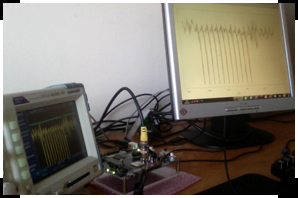
Most embedded devices (e.g. smart card and FPGA) require security and privacy protection. Cryptography algorithms and protocols are designed with the aim to provide such security. However, cryptanalytics attacks based on physical measures (such as the device power consumption named trace) realized on secure devices can be used to challenge their actual security. These attacks called side channel attacks and consist in retrieving secret data by observing physical properties of the device. They are probably among the most dangerous attacks in cryptanalysis.
The DPA Lab[1] is a laboratory for research into side channel attacks and countermeasures based at the Université Libre de Bruxelles (Belgium).
It was established in 2011 by . It is affiliated with the Cryptography and Security Service (CSS) and the Machine Learning Group (MLG) and supported by Atos Worldline (AWL).
It contains computers, oscilloscopes and cryptographic devices. The objective of the DPA Lab is to provide devices in order to allow practical side channel attacks and countermeasures. Examples of such side channel attacks are the timing attacks and the power analysis attacks.

|
|
 |

 |
|


